“Big Data ส่วนใหญ่แล้วไม่ได้อยู่ในเมืองไทย เพราะอะไร ?”
ผมถือว่าโชคดีที่เป็นเด็ก ผมทำงานกับทีมงานอายุไม่มาก กับคนหนุ่มสาวที่มีไฟ (แก้ไขปัญหาเก่ง) จึงทำให้เราได้เรียนรู้อะไรได้ตลอด. ถึงแม้ผมมักจะเป็นหัวหน้าทีม … แต่เวลาทำงาน เราก็ทำเป็นเด็ก คือทุกขั้นตอนการทำงานเรามีส่วนร่วมหมด
เราเรียนรู้และแก้ไขปัญหาการรองรับข้อมูลขนาดใหญ่มานานแล้ว. …..เพราะขายอุปกรณ์และระบบที่ทำหน้าที่เก็บ Log files และวิเคราะห์ข้อมูล ในแบนด์ชื่อ “SRAN”
SRAN นิยมใช้กันในประเทศไทยพอสมควรเมื่อ 10 ปีก่อน
เราสร้าง SRAN มากับมือ. ทั้งเทคโนโลยีที่มาใช้ และ การติดตั้ง มันลงตัวมาก (เมื่อ 15 ปีอัพ)
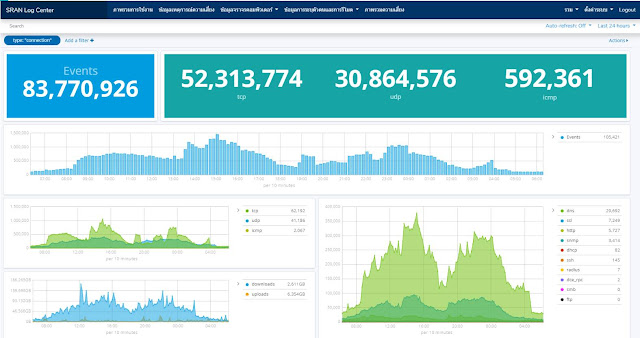
SRAN รองรับข้อมูลเราผ่านระบบเครือข่ายทั้งในรูปแบบของการ Mirror Traffic. จากระบบเครือข่ายคอมพิวเตอร์ และ รูปแบบ syslog server มาเข้าเครื่อง (Appliance) ที่ทำซอฟต์แวร์ในการวิเคราะห์ข้อมูล แยกแยะ Protocol, Application ที่จำเป็นต้องใช้วิเคราะห์ถึงภัยคุกคามที่เกิดขึ้นจากการใช้งานข้อมูล. แต่ทุกอย่างรันบนเครื่องเพียงเครื่องเดียว … ซึ่งมีข้อจำกัดการรับข้อมูลขนาดใหญ่ จะได้เฉพาะหน่วยงานขนาดกลางและเล็กเท่านั้น.
บทเรียนที่เราต้องฟ่าฟันอีกครั้ง เมื่อเราได้รับโอกาส ในงานระดับชาติ ….ซึ่งเรารู้แม้ใส่ Server ราคาหลายล้านก็ไม่ได้สามารถทำได้
เราจึงเปลี่ยนการออกแบบสำหรับเครือข่ายขนาดใหญ่ ข้อมูลขนาดใหญ่ มาเป็นการทำ “Cluster” ราวๆปี 2552 ในงาน Project กระทรวงฯ แห่งหนึ่ง ทำร่วมกับ TOT
ข้อมูล Log ในแต่ละวัน ในสมัยโน้นไม่น้อยกว่า 10G ต่อวัน (ที่มีการบีบอัดข้อมูลแล้ว)
บน Bandwidth เครือข่ายที่เราสู้ได้ตอนนั้นคือ 40G. ย้อนไปเกือบ 10ปีนะ จน Aggregation load balancer. ยี่ห้อที่เรานำมาใช้คือ Anue Network ปัจจุบันนี้ไม่มีแล้ว เราแยกข้อมูลให้วิ่งออกทีละ 1G เพื่อมารับข้อมูลและวิเคราะหในงานนี้ EPS ไม่น้อยกว่า 50,000 session ต่อวินาที กระนั้นเราแทบจะต้านทานข้อมูลมหาศาลที่ไหลมาในระบบเราไม่ได้ หน้าที่ผมตอนนั้นไม่เพียงแต่ออกแบบระบบให้รองรับข้อมูลได้แล้ว ยังต้องเฝ้าระวังให้ระบบพร้อมใช้งานได้อย่างต่อเนื่องอีกด้วย แต่เราก็ผ่านจุดนั้นไปได้
ทีมงานเราได้เรียนรู้ระบบ Cluster มาจากเหตุการณ์นี้ แต่ในสมัยนั้นการทำงาน Cluster. ที่เราทำได้เป็นเพียงระดับ OS และ database. เวลาเราแก้ไขปรับเปลี่ยนโค้ดซอฟต์แวร์ เปลี่ยนทีมงานเขียนโปรแกรม มันทำให้เราต้องทำระบบใหม่อยู่เรื่อยๆ
ผ่านมาเกือบ 10 ปี การเรียนรู้ว่าเราต้องปรับตัว. การปรับตัว คือต้องแสวงหาความรู้. และทดลองทำ เราต้องทำและสู้กับมันอีกครั้ง. เมื่อเกิดสถานการณ์คับขัน. ….
Big Data ที่เกิดได้ง่ายที่สุด คือ เอา Log files มาวิเคราะห์
การออกแบบเราจึงเปลี่ยนไป และเราก็ได้เรียนรู้ว่า เมื่อทิศทางเป็น Cloud computing. แล้วเราจะเอาข้อมูลขนาดใหญ่นี้ไป สิงสถิตถ์ ที่ไหนดี. จะในประเทศ หรือ ต่างประเทศ
คำตอบที่ได้ คงต้องไปพึ่งพวกที่เป็น aws (amazon), google cloud, cloud microsoft azure และ digitalocean. ซึ่งอยู่ต่างประเทศทั้งหมด และยิ่งเรายิ่งห่างด้านเทคนิค บุคคลากร และกระบวนการที่ทำ ยิ่งห่างต่างประเทศ ชนิดที่ไม่สามารถตามทันได้เลย จนมีความจำเป็นที่ต้องไปใช้ข้อมูลฝั่งเขาหมด แบบให้ข้อมูลเขาแบบหมดเนื้อหมดตัวจริงๆ
ในหลายๆครั้ง เมื่อเราได้คุยเรื่อง Big Data ทำไมผมถึงกล้าพูดนักว่า “Big Data ส่วนใหญ่แล้วไม่ได้อยู่ในเมืองไทย”
เมืองไทยยังหาแหล่งสถิตย์ของข้อมูลขนาดใหญ่ นั้นทำได้ยาก(ส์) ทั้งนี้ด้วยเหตุผล 3 ประการ ดังนี้
ขาด Cloud Computing. Infrastructure Management ความพร้อมของ IDC (Internet Data Center) ถึงแม้เรามีหลายเจ้าในประเทศ. “ประเทศเราพร้อมในด้าน Infrastructure แต่ขาดความพร้อมในการบริหารจัดการ”
หากพิจารณาให้ดี ข้อมูลที่เกิดขึ้นนี้จะอยู่ฝั่งนี้จะอยู่ที่ IDC โดยทั้งสิ้น จะทำเป็น Public Cloud Services หรือ จะทำเป็น Private Cloud Services ก็ย่อมทำได้ แต่แล้วทำไหมเรายังขาดเรื่องการบริหารจัดการอยู่อีก เป็นเพราะการบริหารจัดการนั้นไม่ได้เกิดขึ้นจากกระบวนการเพียงอย่างเดียว ส่วนใหญ่แล้วกระบวนการเราผ่าน เราได้ ISO ครบถ้วนที่ IDC พึ่งจะมี สิ่งที่ขาดคือ เทคโนโลยี และ คน
เทคโนโลยี IDC ไหนที่ไม่ใช้ Open Source และเขียนโค้คเองไม่ได้ จะต้นทุนสูงและคืนทุนได้ยาก ซึ่งหากหันไปดู IDC ในไทยโดยส่วนใหญ่ยังติดกับดัก การพึ่งพาเทคโนโลยีที่เป็น Enterprise เกรดจึงไม่สามารถไปถึงขั้นตอนที่กล่าวได้ และลองหันมาดูยักษ์ใหญ่ เช่น Cloudflare, Amazon aws และ Digital Ocean ได้ ไม่มีการใช้. brandname โดยเฉพาะตัวที่เปลืองต้นทุน ไม่ว่า Application Load balancing, Web Application Firewall, แม้กระทั่ง vm virtual machine มักใช้ docker และ open source ส่วน Google และ Microsoft ไปไกลกว่านั้น ยังสร้างเครื่องมือ Tools มาเองด้วย เช่นการเกิดขึ้นของ Kubernetes เป็นต้น
ซึ่งจากกับดักนี้เองทำให้ IDC ในไทยไม่สามารถพัฒนาให้หลุดพ้นการขายแบบธุรกิจโมเดลเดิมที่เคยเป็น เช่นขาย Co-lo, VPS, และ Hosting เป็นต้น
สรุปง่ายๆ ว่า IDC ไหนไม่ใช้ Open Source หรือใช้ไม่เป็นมีหวังเจ๊ง … เพราะ ROI คุณจะคืนทุนเมื่อไหร่ เมื่อเทียบกับการแข่งขันระดับโลกที่สามารถเข้ามาแย่งลูกค้าเรานอกพรมแดนได้ตลอดเวลา เช่น aws, digital ocean และ google cloud เป็นต้น
เมื่อขาดเทคโนโลยี จะทำให้ขาดความพร้อมใน 3 ด้าน คือ ระบบที่ทำงานได้ตลอดเวลา (Zero downtime) , รองรับการขยายตัวในอนาคต โดยไม่ถูกจำกัดด้วยฮาร์ดแวร์ (scalability), Automatic deployment. ยังไม่มีให้เลือกได้ดีเท่าต่างประเทศ.
ส่วนเรื่องสำคัญ คือ คนที่รู้ Open Source ขนาดนั้นจะหาได้ที่ไหน ที่มี skill ที่พัฒนา Tools ได้เองต้องอาศัยความคิดสร้างสรรค์มาก มีจำนวนน้อยมากในประเทศไทย
เป็นเหตุผล ทำให้เราเสียโอกาส. ข้อมูลจึงไหลไปอยู่ต่างประเทศ มากกว่าอยู่ในประเทศไทย
2. ขาดคนทำพวก Application Programming Management.
เราขาดบุคลากร คนที่รู้และปฏิบัติได้ ในการสร้างระบบ เรียกว่า “Microservice” ที่ไว้ค่อยจัดการกับ API และระบบ Automatic ด้านข้อมูล และการจัดการด้านโปรแกรมมิ่ง
การศึกษาของเราไม่ได้สร้างให้เด็กรุ่นใหม่ เรียนรู้กับวิธีการใหม่ๆ. หรือไปไม่ทัน. เราต้องรู้ในแต่ละระดับ เช่นรู้การทำงาน VM แบบ Container โดยใช้ Docker, เราต้องเรียนรู้การบริหารจัดการ Docker อย่าง Kubernetes (google สร้างมา), Docker swarm เหล่านี้คือ Orchestration บนการทำงานแบบ Agile เพื่อการทำเกิด “Resilience System” ทำให้เรายืดหยุ่นและคงทน ไม่ยึดติดที่บุคคล ระบบพร้อมทำงานตลอดเวลา.
“พวกนี้คือตัวเปลี่ยนโลก” ที่อยู่ ระบบ Backend หลังบ้านที่ผู้บริหารไม่สามารถเข้าถึงได้. ส่วน GUI ภายใต้หน้ากากที่ซับซ้อน จะใช้พวก ELK (Elasticsearch, Logstash, and Kibana) ต่อไป ขึ้นอยู่ว่าเราจะออกแบบงานอะไร. จะใช้ Bruffer มาช่วย เช่น radis หรือจะ cluster Hadoop. ก็แล้วแต่จะออกแบบกัน ซึ่งอย่างไรแล้วต้องมี Backend มาก่อนที่ว่ามาก่อน เป็นต้น
ในยุคนี้ ต้องบอกว่าเป็นโลกของ Open Source โดยสมบูณร์แบบอย่างแท้จริง หากใครยังคิดว่า Open Source และ Tools ที่ใช้ open source ไม่มีมาตรฐานล่ะ คุณจะตกการพัฒนาใหม่ๆ แบบตามไม่ทัน ที่กล่าวเช่นนี้ เพราะ code ที่ดีมีคนจำนวนมากช่วยกันปรับปรุง ถูกเก็บการแก้ไขผ่าน ระบบ Github เป็นต้น
ซึ่งทั้งหมดนี้ ประเทศเรายังขาดนักออกแบบระบบแนวใหม่เช่นนี้ อยู่จำนวนมาก. ทำให้เราเสียโอกาสการได้ทำที่ ที่ไว้สิงสถิตย์ของ Big Data
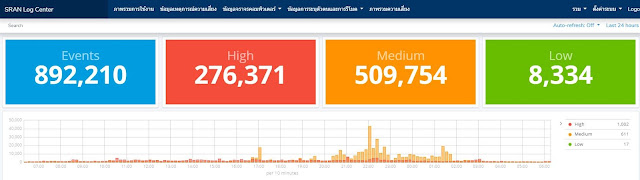
คนไทยที่ได้ทำ ส่วนใหญ่จะมาจากต่างประเทศ หรือได้ลองเล่นสนามจริงในประเทศไทย ก็น่ามีเพียงธนาคาร และที่มีข้อมูลตลอดเวลาเช่น ตลาดหลักทรัพย์ ในการซื้อขายหุ้น และ พวกที่ทำ SIEM Centralized Log Management เป็นต้น ที่จะเข้าใจในจุดนี้ได้
3. เวที ให้แสดงข้อมูลขนาดใหญ่ (ไม่มี)
หากเราจะมี Big Data ได้สมบูรณ์ เราต้องมีการทำระบบวิเคราะห์ข้อมูลการไปให้ถึงในระดับปัญญาประดิษฐ์ Artificial Intelligence (AI) นั้นนอกจากเราต้องมีอะไรบ้าง
อันดับแรกเราต้องมีข้อมูล และข้อมูลต้องบริหารจัดการแบบข้อ 1 และข้อ 2 ที่กล่าวมาได้ เราจึงนำข้อมูลเหล่านี้ มาทำ data science โดยผ่านการคำนวณ แบบ Machine Learning ซึ่งส่วนนี้เมืองไทยไม่ได้ขาดมาก มีผู้เชี่ยวชาญอยู่มาก. มีงานวิจัยอยู่มากในประเทศไทย
แต่เราไม่มีเวทีจริงให้เล่น ให้ลองผิดลองถูก เพราะไม่รู้จะเอาข้อมูลอะไร บริษัทใหญ่เท่านั้นที่มี แอพมือถือรายใหญ่ เท่านั้นที่มี. ซึ่งล้วนแล้วแต่อยู่ในต่างประเทศทั้่งสิ้น.
ไม่ว่าเราจะนำข้อมูลจากที่ไหน Log files เพื่อให้บริการ MSSP, ข้อมูลจาก crawler ข้อความ จาก website, Social network รูปภาพ, ใบหน้าในกล้องวงจรปิด, ข้อมูล transaction การโอนเงิน และอื่นๆ เป็นต้น ซึ่งเป็นข้อมูลที่เกิดขึ้นตลอดเวลา เราต้องทำตั้งแต่ข้อ 1 ถึง ข้อ 3 ที่กล่าวมา. หากขาดข้อใดข้อหนึ่ง ไม่สามารถทำงานได้อย่างมีประสิทธิภาพ
ปล. ข้อดีของการเป็นเด็ก เราจะได้ศัพท์ใหม่ ที่เราต้องรู้กันไป แบบ Life Long Learning. จริงไหมครับ ฝากไว้แบบคร่าวๆ เช่นนี้ โดยเฉพาะข้อ 2 เป็นการออกแบบมีรายละเอียดมากมาย ที่หลายคนมองข้ามไป
นนทวัตต์. สาระมาน
Nontawatt Saraman
15/12/61